
ToyMaker Uses LAGTOY to Sell Access to CACTUS Ransomware Gangs for Double Extortion
Camtruder - Advanced RTSP Camera Discovery and Vulnerability Assessment Tool

Is The Elder Scrolls IV: Oblivion still fun for a first-time player in 2025?
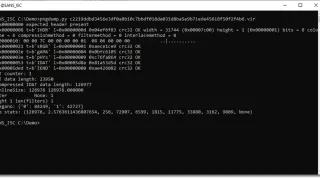
Steganography Analysis With pngdump.py, (Sat, Apr 26th)

Top 5 Open Source Tools to Scan Your Code for Vulnerabilities

Secret Sauce in Robots.txt — How I Found Hidden Admin Panels and Debug URLs
PII Disclosure | CSRF | Open Redirect | CORS Misconfiguration

Path Traversal Attack: How I Accessed Admin Secrets
